Generative AI is revolutionizing cybersecurity with unprecedented capabilities in threat detection, response automation, and vulnerability assessment. As cyber threats evolve at an alarming pace, security professionals are leveraging artificial intelligence to create adaptive defense mechanisms that can predict, identify, and neutralize attacks before they cause significant damage. This transformative technology enables security systems to generate synthetic data for training, simulate potential attack scenarios, and develop countermeasures in real-time – capabilities that were unimaginable just a few years ago.
The integration of generative AI in cybersecurity represents a paradigm shift from reactive to proactive defense strategies. By analyzing patterns across vast datasets, these systems can anticipate emerging threats and automatically generate robust security protocols. From creating sophisticated phishing detection models to developing dynamic security policies, generative AI is empowering organizations to stay ahead of cybercriminals while reducing the burden on human security teams.
As we stand at the intersection of artificial intelligence and cybersecurity, understanding the potential and limitations of generative AI becomes crucial for organizations seeking to enhance their security posture. This technological advancement not only strengthens existing security frameworks but also introduces new possibilities for creating resilient, self-evolving defense systems.
The Evolution of PV System Security Challenges

Common Security Vulnerabilities in PV Systems
Photovoltaic systems face numerous security vulnerabilities that make them attractive targets for cybercriminals. Understanding these cyber threats to PV systems is crucial for implementing effective protection measures. Common vulnerabilities include unsecured communication protocols between inverters and monitoring systems, weak authentication mechanisms in remote access interfaces, and outdated firmware in critical components.
The SCADA systems controlling PV installations often operate on legacy software platforms with known security flaws. Network connectivity exposures through IoT devices and smart meters create additional entry points for attackers. Insufficient encryption of operational data and maintenance logs can lead to unauthorized access and system manipulation.
Physical security vulnerabilities also present concerns, as many solar installations are in remote locations with limited surveillance. Poor access control to junction boxes and control panels can enable direct tampering with system components. These vulnerabilities are compounded by inadequate security awareness among maintenance personnel and insufficient incident response protocols.
Impact of Digital Transformation on PV Security
The digital transformation of photovoltaic systems has introduced unprecedented connectivity and automation capabilities, fundamentally changing how these systems operate. However, this increased interconnectivity creates new vulnerabilities that cybercriminals can exploit. Modern PV installations rely heavily on Internet of Things (IoT) devices, cloud-based monitoring systems, and remote management platforms, expanding the potential attack surface significantly.
Smart inverters and monitoring equipment, while essential for optimal system performance, can become entry points for malicious actors if not properly secured. These devices often communicate with central management systems and utility grids, creating complex networks that require robust security measures. The integration of wireless technologies and remote access capabilities, though beneficial for maintenance and monitoring, introduces additional risk factors that traditional security approaches may not adequately address.
Furthermore, the convergence of operational technology (OT) and information technology (IT) in PV systems means that cyber attacks can have direct physical consequences, potentially affecting power generation, grid stability, and equipment integrity. This evolution necessitates a comprehensive security strategy that considers both digital and physical security aspects, making advanced security solutions like generative AI increasingly crucial for protecting modern PV installations.
Generative AI Applications in PV Security
Predictive Threat Detection
Generative AI models are revolutionizing cybersecurity through their advanced predictive threat detection capabilities. These systems analyze vast amounts of historical security data, network traffic patterns, and known attack signatures to identify potential security breaches before they occur. By leveraging machine learning algorithms and natural language processing, these models can recognize subtle anomalies and patterns that might indicate emerging threats.
The predictive capabilities of generative AI extend beyond traditional rule-based detection systems by continuously learning from new data and adapting to evolving threat landscapes. These systems can simulate thousands of potential attack scenarios, helping security teams understand vulnerabilities and prepare appropriate countermeasures. They analyze user behavior, system interactions, and network communications to establish baseline patterns and flag suspicious deviations.
Key features of AI-powered predictive threat detection include real-time monitoring of system activities, automated risk assessment, and the ability to correlate seemingly unrelated events that may signal a coordinated attack. The technology excels at identifying zero-day exploits and previously unknown attack vectors by recognizing subtle variations in normal system behavior.
Furthermore, these systems can prioritize threats based on their potential impact and likelihood, enabling security teams to focus their resources on the most critical vulnerabilities. This proactive approach significantly reduces response times and minimizes the potential damage from security incidents, making it an invaluable tool in modern cybersecurity strategies.
Automated Response Systems
Automated response systems powered by generative AI represent a significant advancement in cybersecurity for photovoltaic installations. These sophisticated smart security systems leverage machine learning algorithms to detect, analyze, and respond to potential threats in real-time, significantly reducing response times and minimizing human error.
These systems excel in pattern recognition and anomaly detection, continuously monitoring network traffic and system behaviors across solar installations. When suspicious activities are detected, the AI-driven response system can automatically implement predetermined security protocols, such as isolating affected systems, revoking access credentials, or initiating backup procedures.
Key capabilities include automated incident triage, which prioritizes security alerts based on severity and potential impact, and autonomous threat containment that prevents the lateral spread of security breaches. The systems also generate detailed incident reports and maintain comprehensive audit trails for compliance and analysis purposes.
Implementation of these automated response systems requires careful configuration and regular updates to maintain effectiveness. Organizations should establish clear incident response workflows, define escalation procedures, and ensure proper integration with existing security infrastructure. Regular testing and validation of automated responses help maintain system reliability while preventing false positives that could disrupt operations.
Security Protocol Optimization
Generative AI is revolutionizing how organizations approach security protocol optimization by enhancing existing security measures and developing more sophisticated defense mechanisms. Through advanced machine learning algorithms, AI systems continuously analyze security protocols, identifying vulnerabilities and recommending improvements in real-time.
These AI-powered systems excel at pattern recognition, enabling them to detect anomalies in security protocols that might otherwise go unnoticed. By leveraging historical security data and current threat intelligence, generative AI can predict potential weaknesses and automatically generate adaptive security measures to address them.
One significant advancement is the integration of AI with cyber-physical security systems, which creates a more robust and responsive security infrastructure. This integration enables dynamic protocol adjustments based on real-time threat assessments and system performance metrics.
AI-driven security optimization also includes automated protocol testing and validation, reducing the time and resources required for security assessments. The technology can simulate various attack scenarios, evaluate protocol effectiveness, and suggest improvements before implementation in production environments.
Furthermore, generative AI assists in developing new security protocols by analyzing emerging threats and creating innovative defense strategies. These AI-generated protocols often incorporate advanced encryption methods, authentication mechanisms, and intrusion detection systems that evolve alongside new security challenges.
Implementation Strategies and Best Practices
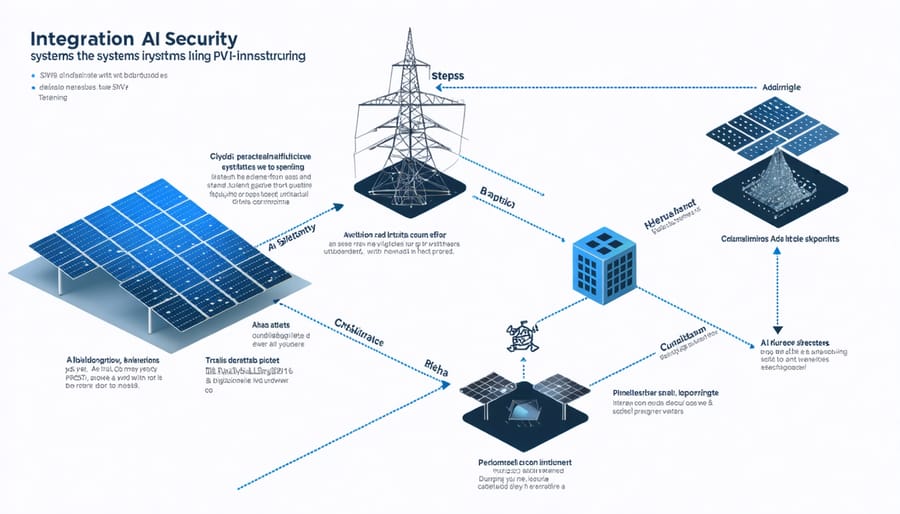
Integration Framework
Implementing generative AI security systems requires a systematic approach to ensure effective integration with existing cybersecurity infrastructure. The process begins with a comprehensive assessment of current security protocols and identification of potential integration points. Organizations must first establish clear security objectives and compliance requirements before proceeding with implementation.
The initial phase involves data preparation and system configuration. Security teams should collect and curate high-quality training data, ensuring it represents various threat scenarios and attack patterns. This data forms the foundation for the AI model’s learning process and threat detection capabilities.
Next, organizations need to select and configure appropriate AI tools and platforms that align with their security requirements. This includes setting up necessary hardware infrastructure, establishing secure communication channels, and implementing access controls. The integration process should follow a modular approach, allowing for incremental deployment and testing of different security components.
Testing and validation form a crucial step, where the AI system undergoes rigorous evaluation in a controlled environment. This includes penetration testing, vulnerability assessments, and performance monitoring. Organizations should establish metrics for measuring the effectiveness of the AI security system and conduct regular audits.
Finally, the implementation process should include continuous monitoring and refinement mechanisms. This involves regular model updates, performance optimization, and adaptation to new threat patterns. Staff training and documentation are essential components to ensure proper system operation and maintenance.
Risk Management Considerations
When implementing generative AI solutions for cybersecurity in photovoltaic systems, organizations must conduct a thorough PV security risk assessment to identify potential vulnerabilities and establish appropriate safeguards. Key considerations include data privacy compliance, model training integrity, and the potential for adversarial attacks on AI systems.
Organizations should establish clear governance frameworks for AI deployment, including regular security audits, model validation protocols, and incident response procedures. It’s crucial to maintain human oversight of AI-driven security decisions while implementing fail-safes to prevent system compromises.
Data quality and bias management are essential factors, as AI models require accurate, representative training data to function effectively. Regular model retraining and validation help ensure continued effectiveness against evolving threats while minimizing false positives that could impact system performance.
Integration with existing security infrastructure demands careful planning to avoid compatibility issues and maintain operational continuity. Organizations should also consider the scalability of AI solutions as system requirements grow and develop contingency plans for AI system failures or compromises.
Investment in staff training and expertise development ensures proper system management and maintenance, while documentation of AI decision-making processes supports accountability and regulatory compliance. Regular assessment of AI performance metrics helps optimize security outcomes and justify continued investment in these technologies.
Future Perspectives
The landscape of generative AI in cybersecurity continues to evolve rapidly, promising transformative developments for the protection of photovoltaic systems. Industry experts anticipate several key advancements that will reshape security paradigms in the coming years.
Machine learning models are expected to become increasingly sophisticated in their ability to predict and identify novel cyber threats. These systems will likely incorporate more advanced anomaly detection capabilities, enabling them to recognize subtle patterns that might indicate emerging attack vectors before they materialize.
Integration of quantum computing with generative AI presents particularly exciting possibilities. As quantum computers become more accessible, they will enhance the processing power available for security algorithms, potentially revolutionizing encryption methods and threat detection speed.
Automated response mechanisms are projected to achieve new levels of autonomy and effectiveness. Future systems will likely feature self-healing capabilities, automatically implementing defensive measures and system repairs without human intervention, significantly reducing response times to security incidents.
Cross-platform integration is expected to become more seamless, with generative AI systems operating cohesively across different PV components and security layers. This integration will create more robust, unified security frameworks that can protect entire solar energy infrastructures more effectively.
Edge computing implementation in PV security systems is anticipated to grow, enabling faster local processing of security data and reduced latency in threat response. This development will be particularly crucial for remote solar installations where immediate cloud connectivity isn’t always available.
Researchers are also exploring the potential of federated learning systems, which will allow multiple PV installations to contribute to collective security knowledge while maintaining data privacy. This collaborative approach could significantly enhance the industry’s ability to identify and respond to emerging threats.
However, these advancements will need to address challenges such as AI model transparency, ethical considerations, and regulatory compliance. The industry must maintain a balance between innovation and responsible implementation to ensure these technologies serve their intended purpose while protecting user privacy and system integrity.
As we’ve explored throughout this article, generative AI represents a transformative force in cybersecurity for photovoltaic systems and renewable energy infrastructure. The integration of AI-powered security solutions offers unprecedented capabilities in threat detection, response automation, and predictive analysis, making it an essential component of modern security frameworks.
The adoption of generative AI in cybersecurity brings multiple advantages, from enhanced anomaly detection and real-time threat response to improved incident analysis and automated security testing. Organizations implementing these technologies have demonstrated significant improvements in their security posture, reducing response times and minimizing potential vulnerabilities.
However, successful implementation requires careful consideration of challenges such as data privacy, algorithmic bias, and the need for skilled personnel. Organizations must develop comprehensive strategies that balance innovation with responsible AI deployment, ensuring compliance with regulatory requirements while maintaining system integrity.
Looking ahead, the continued evolution of generative AI technology promises even more sophisticated security solutions. As threats become more complex, the role of AI in protecting critical infrastructure will only grow in importance. Organizations that proactively embrace these technologies while maintaining robust security practices will be better positioned to defend against emerging cyber threats.
For maximum effectiveness, security professionals must stay informed about advancing AI capabilities, participate in ongoing training, and foster collaboration between AI developers and cybersecurity experts. This proactive approach will ensure the successful integration of AI-enhanced security measures while maintaining the highest standards of system protection.







